AmRRON Dark Labs: ADL-1 OTP Generator
 Most of the readership is at least familiar with the American Redoubt Radio Operator’s Network (AmRRON), a radio organization dedicated to communications among operators in the American Redoubt region but also nationwide. They hold several regular exercises and events aimed at getting preppers on the air, networked and using their equipment with a more grid-down focus than most conventional radio operators normally would.
Most of the readership is at least familiar with the American Redoubt Radio Operator’s Network (AmRRON), a radio organization dedicated to communications among operators in the American Redoubt region but also nationwide. They hold several regular exercises and events aimed at getting preppers on the air, networked and using their equipment with a more grid-down focus than most conventional radio operators normally would.
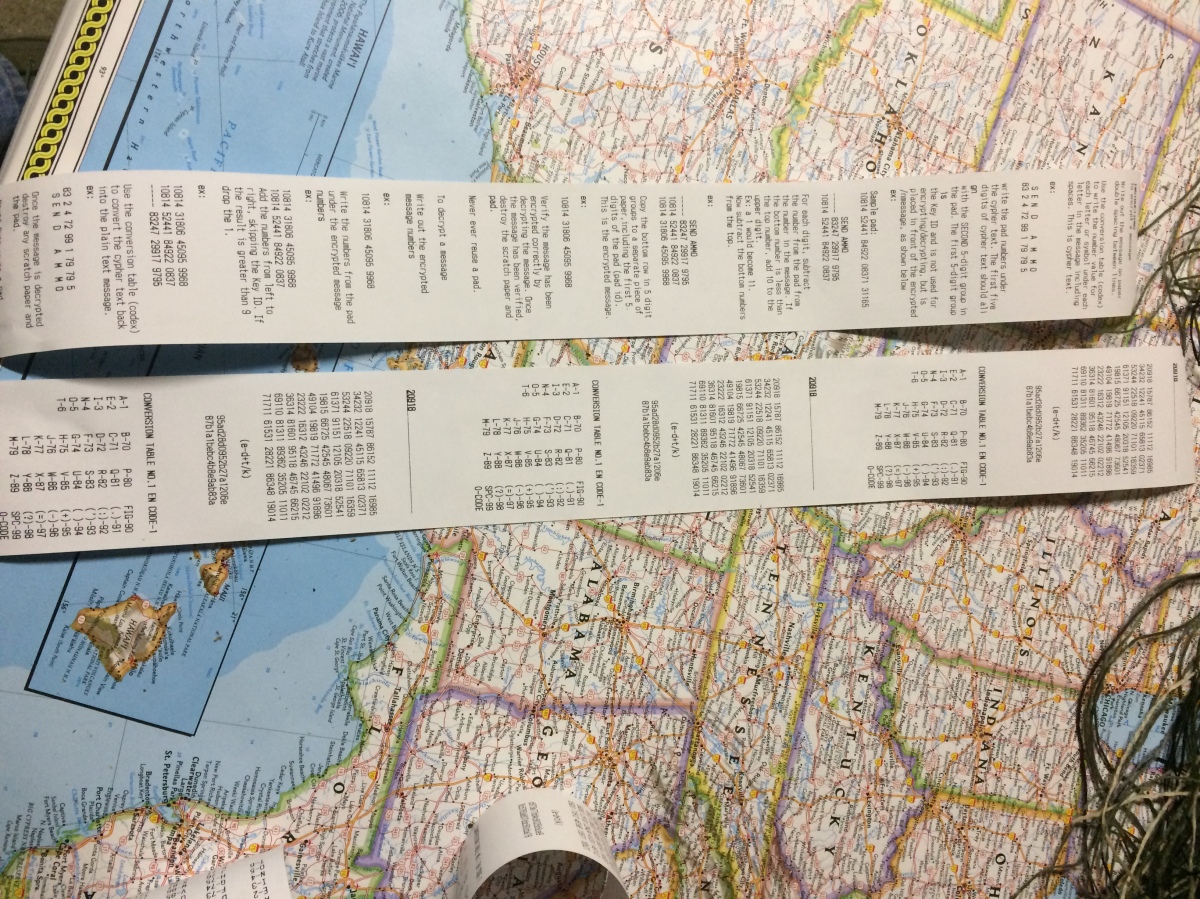
It should come as no surprise that in addition to the ability to communicate off-grid, many desire a need to encode messages and its a frequent question I get in emails. People value their privacy and there’s no simple answer; those of you who’ve asked me know that I always start with, “it depends”. Tactical communications, being local and immediate in nature, have a different focus than longer term situation reports or intelligence cables which deal with regional, infrequent communications. Whether these are over the air or sent by a messenger, one of the older and still most effective forms of encryption for the latter is by the use of a One Time Pad (OTP). One of the ways to do this and guarantee generating truly random numbers is through the use of 10 sided dice, rolling and writing the numbers down on a pad. This is highly time consuming, especially since each series of numbers is only used once and some messages are hundreds of characters long. AmRRON Dark Labs, a type of Skunk Works for the Patriot community, has built a machine which makes the whole process much easier- the OTP generator. How do we use the OTP? Check out this simple practice exercise to get you up to speed.
 This is a device designed to be used. Enclosed in a pelican-type case, I have no issue packing this into a ruck and carrying it into an area of operations. There’s no worrying if it gets dinged up. Further, the Dark Labs team have essentially made the device idiot-proof, meaning for most of us we can use it even when we’re running low on caffeine and that’s something I highly appreciate. As you can see in the photo, there’s only four buttons for the controls and the whole system can be up and running in seconds. It uses two 18650 Lithium Ion batteries which provide an incredibly long battery life. I charged these once and have been using it intermittently for over a month and the device shows no signs of dying. So long operation in the field and off-grid is not a problem.
This is a device designed to be used. Enclosed in a pelican-type case, I have no issue packing this into a ruck and carrying it into an area of operations. There’s no worrying if it gets dinged up. Further, the Dark Labs team have essentially made the device idiot-proof, meaning for most of us we can use it even when we’re running low on caffeine and that’s something I highly appreciate. As you can see in the photo, there’s only four buttons for the controls and the whole system can be up and running in seconds. It uses two 18650 Lithium Ion batteries which provide an incredibly long battery life. I charged these once and have been using it intermittently for over a month and the device shows no signs of dying. So long operation in the field and off-grid is not a problem.

To start the process, hit the switch and press the graph button on the far left to set the number of digits. Next press the gear button to begin the generation of numbers. When you do this the Ready LED will flash orange, then green. Green indicates the pad has been generated and is ready to print. You can press the lined button to the right of the gear button to select whether you want just the Pad, the Pad plus Codex (the conversion table) or just the instructions, which generously print the method to use the OTP. Once you’re ready, hit print.

You can print as many of the same Pads as you need by hitting print repeatedly. The firmware includes a five minute timer on the pad, so that once the time period has expired, the pad is erased and cannot be retrieved. The whole process cannot be simpler or more convenient when equipping groups with pads for use over a period of time.
Now we’ve got three pads- one for the TOC and two our teams, all serial numbered and ready for distribution. Quick, simple, and a heck of a lot faster than generating them by dice.
[et_bloom_inline optin_id=optin_4]From using this device I can say it works exactly as advertised. It’s one of the very few pieces of gear that I can honestly say I have no complaints with and its simplicity is its strength. Some of the early concerns on the AmRRON site were questioning the true randomness of the number generation. But the code itself is open source for you to modify and the firmware is easily updated on the machine. They leave it up to you, as you need it. I haven’t made any changes because I don’t think its necessary, especially after seeing the robustness and simplicity of the generator as is. It does indeed generate random numbers- and the better bet for an opposing Intelligence Multi-Function Team (MFT) would be to simply intercept the sender/source then try to break it. It just eats up too much time for too little gain, especially if a group is also using a Brevity Matrix for another layer of security before encoding the message. I highly suggest this device for groups of preppers networked over a region that may be wanting to share sensitive information or if they’re just wanting that old Enigma Machine vibe. Pick up one today and support those that support you- we take care of our own.
A big thanks to AmRRON and the Dark Labs team for asking me to provide an end-user assessment of the machine.

Share This Story, Choose Your Platform!
11 Comments
Comments are closed.





































4
5
4.5
4.5
[…] patrol at times the Opposing Force (OPFOR) are less likely to be listening. These are encoded via One Time Pad. Miss two commo windows in a row, and the focus of the operation now becomes personnel recovery. […]
5
“This is highly time consuming, especially since each series of numbers is only used once and some messages are hundreds of characters long.”
Excuse my ignorance, but don’t the numbers need to be generated for all the letters and symbols for each communication, then re-used as often as needed within that message before being disposed of? How would the length of the message to be encoded change how many times the dice would need to be rolled for that message?
A one time pad is only used once. You have to roll the ten sided die for each number (which corresponds to a letter).
Copy that. But whether your message was 10 characters long or 1000, you’re still only using a 26 letter alphabet (or more with symbols and numbers – if you didn’t want to spell them out) and each letter would be only need to be rolled once to create the OTP for THAT message. Which means no matter the length of the message, you’re rolling 26 times….correct? I want to make sure i’m not missing anything. Cool machine. Good price. Thx for sharing!
That’s incorrect. What you’re creating by rolling the dice is a key. Since you have no idea how long a potential message may be in the planning phase of an operation, they need to each be as long as possible to maximize the number of usable characters. The OTP-1 makes the process much faster.
I cover using OTP encryption in my Advanced RTO course, after we cover using a brevity matrix. Once you’ve cut down a large message into a compressed form with the BREVMAT, you then encode it with the OTP.
[…] as the AmRROM[1] Dark Labs ADL-1 OTP Generator. My colleague NC Scout did a review of the system here, and I also own a system and can personally vouch that the generator makes pad creation infinitely […]